Microsoft’s antivirus is in itself quite reliable as it is installed and configured. However, if we want to go a little further, we can apply some changes and configurations that we can make to further improve its performance if we are concerned about security and want to avoid being a victim of any type of malware at all costs.
Schedule and run full scans with Windows Defender
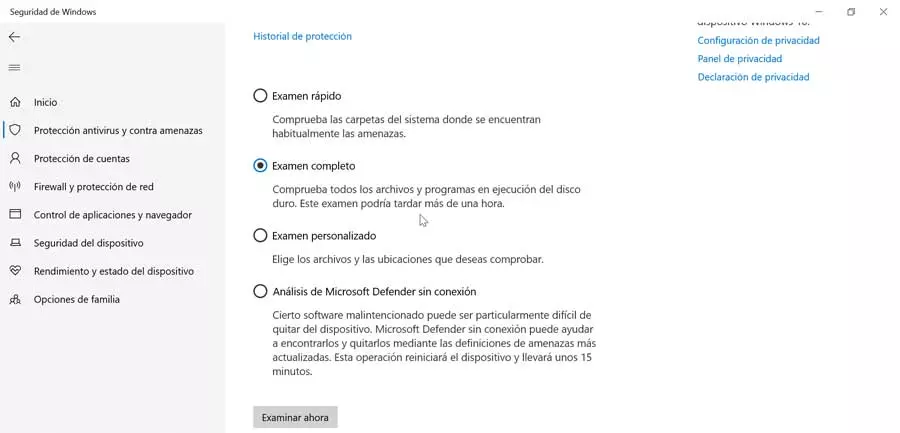
Perhaps the most well-known section of an antivirus is the possibility of carrying out scans to verify that there is no intruder in our system that should concern us. Defender has an always-on and real-time protection that checks the files and folders every time we open it. In addition, we can perform a full system analysis, performing an exhaustive check of all the files, disks and drives of the system, both internal and external. If we are in doubt that we may have a virus, it is the best option to check it.
In the same way, we may not want to carry out this type of scan when we are in front of the PC, as it can slow down the use of other applications. Therefore, before avoiding its use, we can opt for the scan scheduling, which allows us to choose the day and time in which we want to perform the analysis. This is something we must do through the “Windows Task Scheduler”.
Essential protections that we must activate
To ensure that we are protected against any type of threat, there are some Windows Defender settings that we must always keep active. One of the most important threats is ransomware that encrypts files and systems. Microsoft’s antivirus has Protection against ransomware, which we must make sure to activate. From this section we can manage and configure the protection if we activate this option. We can find it in its section “Antivirus protection against threats”.
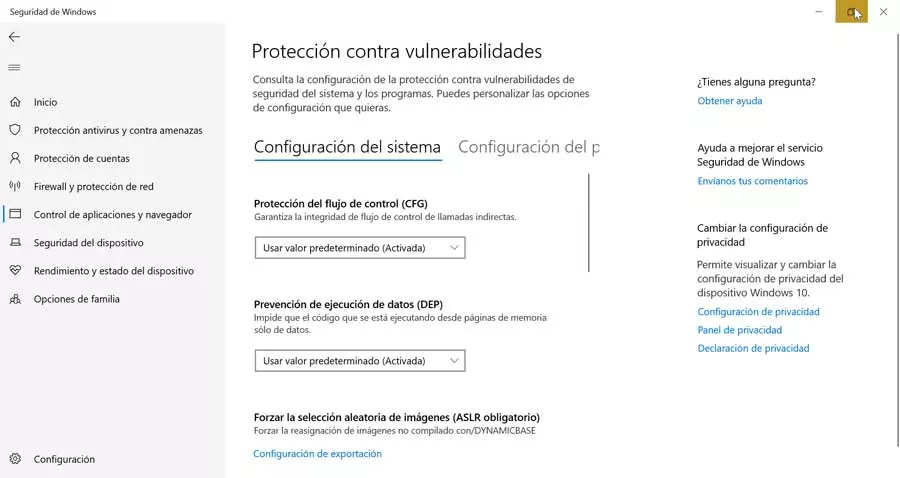
On the other hand, we must also have activated the Protection against vulnerabilities, from where we can see all types of vulnerabilities and take charge of keeping them under control. Do not forget that system vulnerabilities can be the main objective of hackers to gain control of our computer. We can access it from the “Application and navigation control” section.
In addition, we must not forget to activate the Firewall, and that will help us to filter which programs may or may not have access to the Internet, allowing us to choose whether we want a public or private network, depending on where we are going to frequently connect to the Internet from. To maximize your protection we can create new rules in the Firewall and thus obtain an even more exhaustive control.