There is no doubt that communication between people has made a huge change with the internet, not only with regard to communication with others and therefore the transmission of information, but also with regard to electronic commerce where the bank details of hundreds of millions of People circulate on the network and it is necessary to use much more advanced protection systems than usual, such as reliable computing hardware modules.
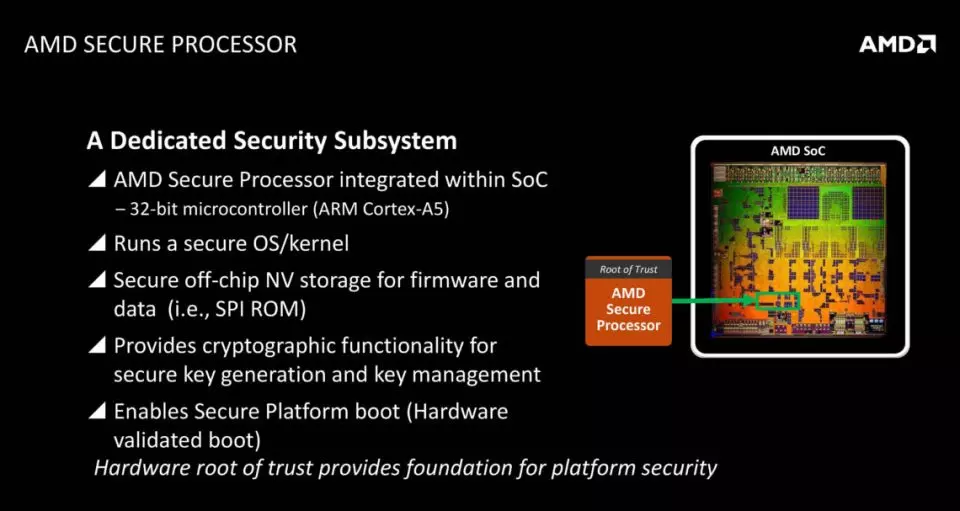
Having our data stored in a memory space that can be accessed from the CPU is not safe since there are methods to bypass the security methods of protecting the central processor of the PC. That is why it is necessary to store private data in memories in which it is not easy to access by the central processing unit and therefore have a guardian. Today we know that a bug in a security update from AMD has put its processors in check. Let’s see what happened.
AMD back to the fore, how serious are its security update bugs?
No, we are not alarming anyone or launching any speculation, but this comes from the manufacturer of Ryzen processors, who have just released information about a vulnerability in their CPUs as the effect of a recent update in the drivers. The vulnerability was discovered by cybersecurity researcher Kyriakos Economou, co-founder of ZeroPeril.
Kyriakos Economou himself has described the vulnerability in the following words:
During our tests we have managed to filter out several gigabytes of uninitialized physical pages, re-locating and releasing blocks of hundreds of locations in a continuous way until the system has not been able to return the buffer of the adjoining page.
The contents of those physical pages range from kernel objects to arbitrary address wells that can be used to bypass exploit mitigation methods like KASLR, and even (Windows) registry items like keys stored in Registry Machine SAM that contains NTLM hashes of user authentication credentials that can be used in later stages of the attack.
For example, (such credentials) can be used to steal credentials of a user with administrative privileges or in pass-the-hash style attacks to gain more access within a network.
As you can see, it is a very serious problem, now, despite its magnitude, this has already been solved, let’s see how.
Is my PC with AMD CPU in danger, is there a solution?
Through a joint work between both companies they have been able to solve the problem in the newer CPU drivers, which are also included in the latest version of Windows Update. What’s more, the patch has been online for several days, the difference is that AMD released it by updating modules and has now recently recognized it. The security failure in the update of AMD CPUs is due to the exploitation of current hardware, which has been compromised several times in the past as happened to its maximum rival.
And which AMD processors and chipsets have been affected? Well, the APUs and CPUs equipped with the AMD Platform Security Processor, which includes the AMD Ryzen in all its generations: from the 1000 to 5000 ranges regardless of whether we are talking about CPU or APU and are these for laptops or desktops. In addition, it affects not only CPUs with Zen architecture, but every AMD processor that has been released from 2012 onwards.
AMD has plans to replace its Platform Security Processor starting in 2022 with the launch of the Ryzen 7000 APUs and CPUs, which will be the time when they will first integrate the HSP / Pluto security processor developed jointly by Intel, AMD, Microsoft and Qualcomm. . The reason for this is that pieces of hardware such as the Intel Management Engine or the AMD PSP have not proven themselves to be good enough to provide a reliable enough environment.
Therefore, the solution to this vulnerability from AMD has been corrected using its latest chipset drivers, specifically with version 3.08.17.735, which you can download from the manufacturer’s website by following this link.